Key Tracking Software







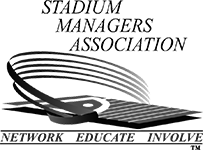

Software to Streamline Your Key Management System
Mechanical lock and key systems are the first line of defense in maintaining your security. Which means that having a comprehensive key management system is crucial to controlling and monitoring secure keyed access for your organization. Our patented, cloud-based key tracking software modernizes the way you manage your key system.
SecurityRecords.com® gives you visibility and control over all aspects of your key system with easy-to-use dashboards and real-time updates.
Key tracking software can give you control of your key system in a way that paper files, spreadsheets, or PC-based software can’t. Poor key management can compromise your security, be a hassle to manage, and cost you time and money. No matter what lock and key system you have in place, InstaKey’s key tracking software can help you better manage your keyed security. Here's where you can see how SecurityRecords.com® stacks up against it's competition.
What SecurityRecords.com® Can Do For You
Get real-time visibility into:
- Each key, specific locations and doors it accesses, and who is responsible for it
- What keys have been made and which locks have been changed, including how often and why
- Who has access to your key software data and records of modifications that have been made
- Quick investigation and resolution in the event of a keyed security breach, easy change of access with employee turnover, and streamlined key audits
- Improving procedures around key management and costs
- Creating tighter controls and improving accuracy and accountability for loss prevention and asset protection
- A dashboard tracking of frequencies, orders, supplier turnaround times, and freight costs
- How your entire key system is operating from top to bottom
Take complete control of your key system information with SecurityRecords.com®. You can manage, share, integrate and audit your key system data to enhance compliance and reduce costs. Easy, comprehensive key management is within reach!
Explore SecurityRecords.com®
For a demonstration of the Key Control Administration Console (or SecurityRecords) let us know.
Key Tracking Data at a Glance
Real-Time, Actionable, Key System Performance Dashboard
When you log in to SecurityRecords.com®, you’ll see your real-time KeyControl Program dashboard. This is where authorized key system administrators can get an accurate and up-to-date look at a variety of performance metrics. Each dashboard report is actionable. Simply click on a report to drill down into the data. Here's a look at the reporting available:

Rekeying Analysis

Key Transitions
When you get restricted keys back from key holders, reassign them easily and keep track of how often key transitions occur. With InstaKey’s user-rekeyable cores, you can eliminate the need for rekeys after a key transition to save both time and money.

Rekeyable Cores Step Tracking
Easily track your InstaKey user-rekeyable cores on your dashboard. Rekeyable cores can be rekeyed up to 9 times, depending on the type of key system. You can see which step your cores are on right from the dashboard.

Locations Installed
Keep track of what locations are installed with InstaKey. Use this information to run a cost comparison on specific locations or types of hardware. You can easily search by location to find the address, contact information, notes, keys, doors, and users relevant to that facility.

User Activity

Order Analysis

Freight Analysis

Order Management

Order Turnaround
Key Tracking and Key System Updates
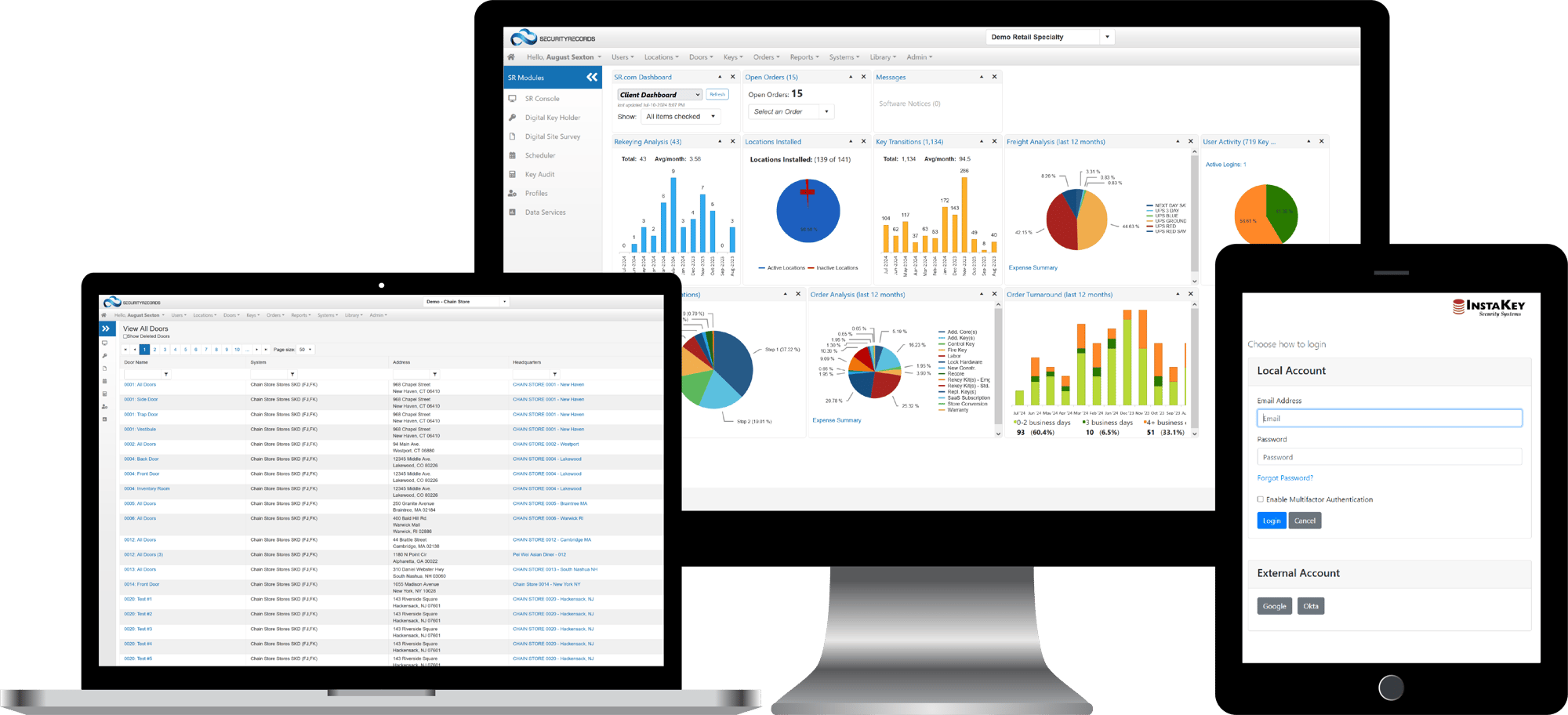
SecurityRecords.com® makes looking up and/or updating any component (locations, doors, keys, users) of a key system simple. View data broadly or isolate to any specific component by using the navigation drop-downs just above the dashboard. Easily search for, view, and update locations, doors, users, and keys throughout your day-to-day key management. Need to easily create and export reports for additional analysis? SecurityRecords.com® can do that too. Export reports on active keys, unassigned keys, rekeying analysis, users and more! You can also create custom reports to meet your internal key management needs.
Advanced Key System Management
There are several additional modules available in SecurityRecords.com that can perform more advanced functions of KeyControl. When utilized, these modules can save a considerable amount of time and create more opportunities for contactless key system management.
 The most basic purpose of KeyControl is controlling who has access to what. That is why our keys are restricted and serialized.
The most basic purpose of KeyControl is controlling who has access to what. That is why our keys are restricted and serialized.
Restricted keys cannot be duplicated. This allows organizations to assign keys to key holders with the peace of mind, knowing that user will remain the only person with that key and access.
Unique serial numbers act as key fingerprints that when assigned to a key holder, that number follows the user and makes it easily tracked when transitioned between users. When keys are returned by departing key holders, the serial number is just another safeguard that verifies the key issued is the key returned.
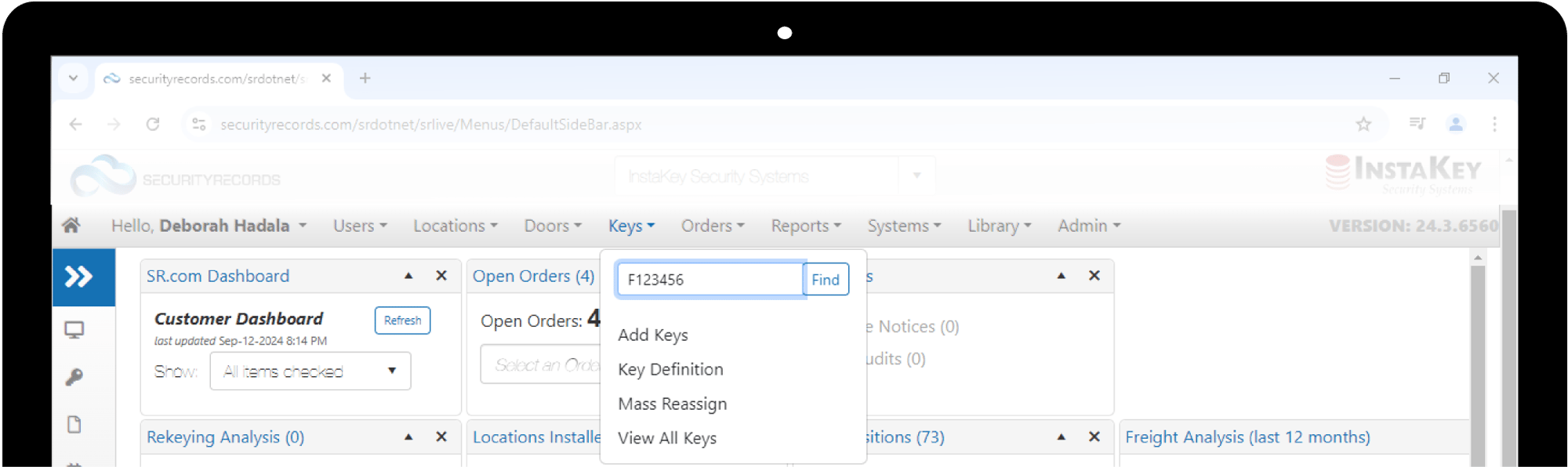
Another piece to controlling access when issuing keys is a document called a Key Receipt. This is an agreement between the organization and the key holder regarding the expectation for key custody and the safeguarding of keys. A basic Key Receipt documents the key serial number(s) and the user in custody. The user signs the agreement which also includes the expectation for what should happen if a key is lost or stolen, and any applicable consequences or costs for key replacement.
As administrators are making updates to key custody in SecurityRecords, Key Receipts can be sent and signed remotely using any smart device. Once signed, this electronic document is automatically appended to key system records to be viewed at any time in SecurityRecords.com.
 KeyControl best practices include performing regular audits. If administrators are assigning keys and documenting key serial numbers in the process, a digital audit process can save time and make the audit process contactless. With the Audit tool in SecurityRecords, administrators can automate the process of auditing keys and who has custody of them, without having to be on-site with key holders.
KeyControl best practices include performing regular audits. If administrators are assigning keys and documenting key serial numbers in the process, a digital audit process can save time and make the audit process contactless. With the Audit tool in SecurityRecords, administrators can automate the process of auditing keys and who has custody of them, without having to be on-site with key holders.
There are three different types of audits available:
Listed Audit: This type of audit allows administrators to send out a list of serial numbers (on keys) to key holders via text or email. Those communications include a link that allows key holders to confirm what they have.
Unlisted Audit: This audit will send an email or text a link to key holders that will prompt them to list the key serial numbers they have, which will match those serial numbers with the records on file.
Listed and Unlisted Audit: This is a combination of both audit types listed above. It works the same as the listed key audit, but key holders can add to what they've been assigned, allowing for additional input. For example, if for some reason a key holder leaves the organization and gives their keys to another key holder, the remaining key holder can list those in this type of audit.With Audit, administrators have access to real-time updates on how an audit is progressing to be able to gauge areas of progress and hindrances, offering a high-level summary as well as InstaKey feedback on possible actions needed. Each type of audit can be set up to run monthly, quarterly or whenever it is necessary.
Audit becomes more powerful and robust when other functions in SecurityRecords.com are more broadly utilized, such as Hierarchies and Key Definitions. Audits are easier to run when key Hierarchies are set up to include email addresses and phone numbers of key holders. Using Key Definitions allows administrators to audit by key name.
 Gearing up a new location? Considering converting locations over to InstaKey? The first step in getting a new location set up with InstaKey is a site survey. Typically, a locksmith is commissioned to perform this task, documenting the lock hardware used in each door, fixture, etc.
Gearing up a new location? Considering converting locations over to InstaKey? The first step in getting a new location set up with InstaKey is a site survey. Typically, a locksmith is commissioned to perform this task, documenting the lock hardware used in each door, fixture, etc.
Your time is valuable. You shouldn’t have to wait for a locksmith to survey existing hardware when you are considering a lock system conversion. Locksmiths are expensive too. Most locksmiths will charge $150 just to visit one location, then they charge on top of that to survey hardware. Before you can even decide if a conversion is right for your locations, you’ve already spent hundreds or even thousands, without having any new lock hardware to show for it. It’s time to put a stop to this – with Digital Site Survey (DSS).
Use DSS to survey locations whenever it's convenient for you. Use your smart phone or other WiFi-enabled device to snap hardware photos and submit them to InstaKey hardware experts for analysis. If, for whatever reason, you decide not to convert your sites to InstaKey, you pay nothing. If you decide to convert to InstaKey, you’ll be billed a nominal fee when we build your order. That cost is based on building size, which translates to what is needed of a hardware expert’s time. That cost is usually only 10% of what you would have paid a locksmith.
Site surveys are routine. Let’s make them easier and cheaper.
 Instead of having Security Records users manually enter data, let InstaKey Data Services do the heavy lifting. Upload both HR and Location Data from the source and improve data accuracy and timeliness. Data can be sent either by our Web API or as a simple flat file sent via our secure FTP. Once the data is uploaded, it is available immediately and is synced across the entire suite of InstaKey products. Uploads process new entries as well as update existing ones with your most recent data.
Instead of having Security Records users manually enter data, let InstaKey Data Services do the heavy lifting. Upload both HR and Location Data from the source and improve data accuracy and timeliness. Data can be sent either by our Web API or as a simple flat file sent via our secure FTP. Once the data is uploaded, it is available immediately and is synced across the entire suite of InstaKey products. Uploads process new entries as well as update existing ones with your most recent data.
Do you utilize or store key data in another system? InstaKey Data Services can work with your IT teams to provide Security Records key information to other systems in real time. This can provide user and key population data, active location data, and even shipping information pertaining to your orders. Whatever the need, InstaKey Data Services can assist you in getting the information you want, when you need it.
A Key Control Program is only as effective as the tools you use to manage it. The key tracking software known as SecurityRecords.com® is the most effective way to manage a key system and control associated costs. Access it from anywhere in the world with an internet connection, and rest assured that it is always accurate and up-to-date, even when used by multiple key system administrators. Get started with InstaKey’s SecurityRecords.com® by talking with a security expert.


