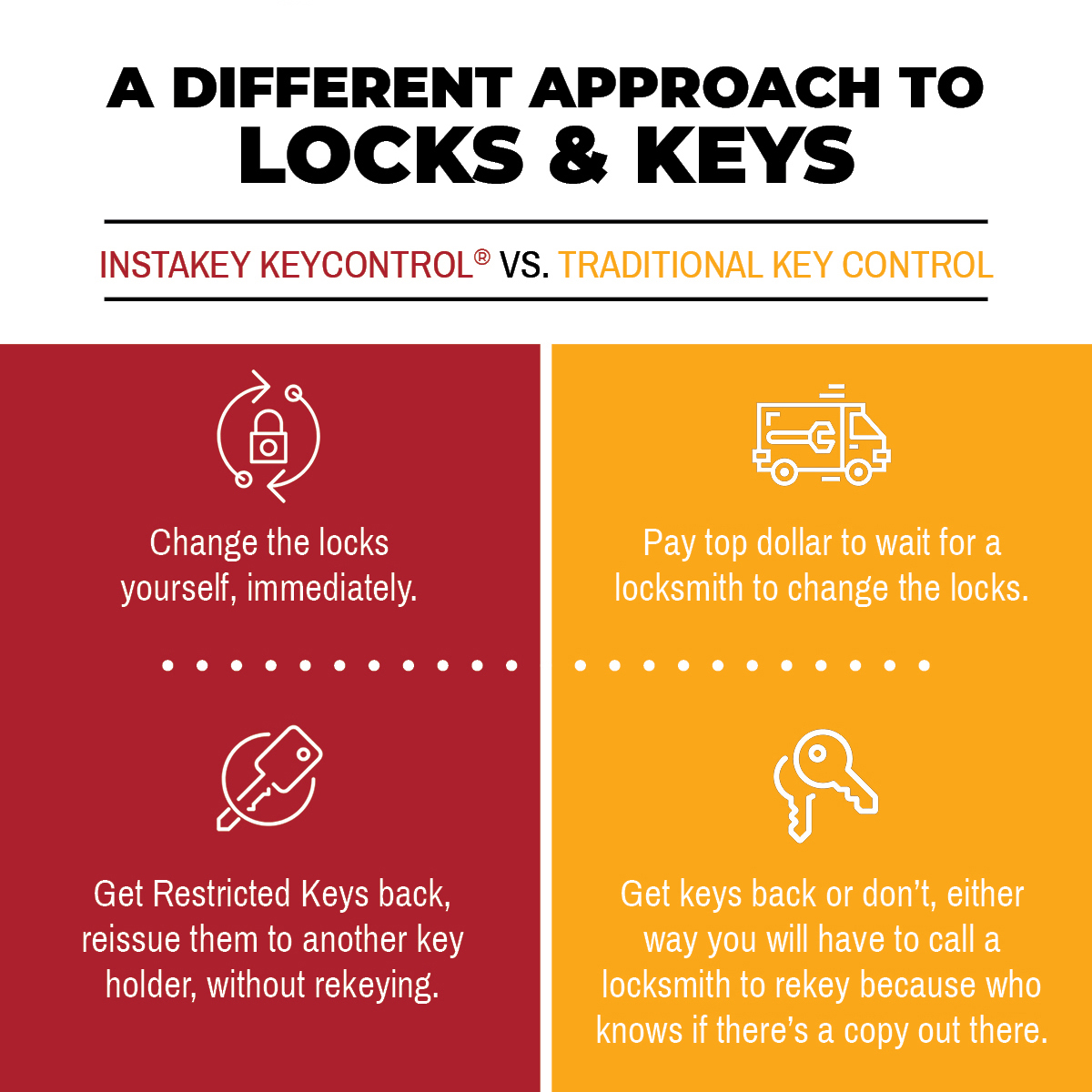
An InstaKey® KeyControl program saves time and money, but what is it?
key con·trol
/kē kәn’ trōl/
noun
Refers to various methods for making sure that mechanical keys are only used by authorized people.
Creating an effective key control program for your organization is crucial to ensuring the security of your assets. If you can effectively manage keys so that they are only being used by the people who are authorized to have them, you limit the potential for keyed access security breaches. And if you can proactively address a breach with speed and accuracy before it occurs, you’ll be saving time and money. InstaKey® incorporates four innovative elements of KeyControl to form a comprehensive program around controlling locks and keys quickly and cost-effectively.
Restricted Keyways
Our restricted, serialized keys are only available through us. In other words, a restricted key cannot be copied. We tightly control our restricted keys through licensing agreements instead of through patents because eventually, patents expire. On top of that, each and every key is stamped with a unique serial number to ensure that each key is genuine. This also makes it easy to keep track of keys. When a key is returned by a designated key holder, key system administrators can rest assured that there is not a copy of that key in circulation that will threaten the security of assets. That key can then be transitioned to a new user, without any hassle needed to change the locks.
User-Rekeyable Locks
In the event that a key is lost or stolen, corresponding locks will need to be rekeyed. Rekeyable locks eliminate the need for a locksmith’s expertise (and fees) because they can be rekeyed immediately by authorized personnel instead. No tools necessary. No hardware removal. A Step Change key is all that is needed to restore the security of your assets. This significantly lessens the need for copious storage of spare key cores necessary with core swap programs. A user-rekeyable lock can be rekeyed up to nine times before the cores need to be swapped out for another set of nine rekeys.
Key Tracking Software
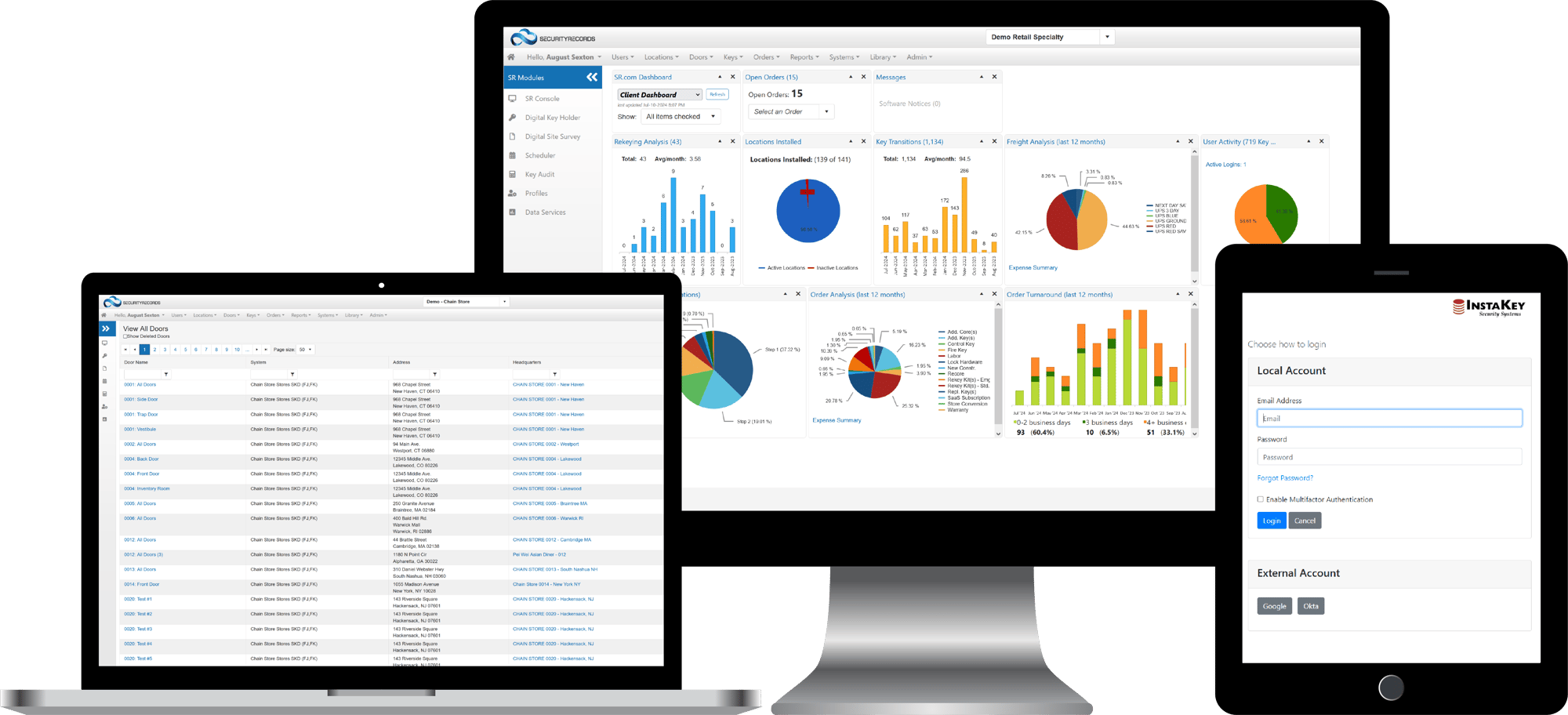
In order to keep track of keys and increase key holder compliance, we’ve developed SecurityRecords.com® – a method of tracking keys to key holders using unique identifiers on keys (serial numbers or other markers). All records and associations between keys, key holders, cylinders, doors and locations are stored in the cloud and accessible 24/7, from anywhere in the world. And you don’t have to use InstaKey keys and locks to track keys. In the event of a keyed access security breach, you’ll have quick access to a list of key holders to examine in the event that an investigation is necessary. Not only does the software come in handy for keeping track of keys, it helps administrators track the cost and performance of a key system as a whole. Learn more with our Key Tracking Guide or Key Tracking Comparison.
Program Administration
All of our KeyControl programs are managed, to some degree, through partnership with InstaKey, but your organization might need some additional support. You may not have the resources to focus closely on the security of your key system. Enter InstaKey Program Administration. We will manage your key system for you, at any level you need, from periodic consultation to full program administration.
Key Control Resources
We know that not everyone is as key-focused as we are, and that effective key control is a big topic to cover. Additionally, some of the language used in the industry can be confusing if you’re not talking locks and keys all day like we are. We cover some big topics about key control in the resources below, as well as on our blog, to provide more clarity to what each aspect of an effective key control system is, how it works, and what it can do for your organization’s overall security and operations.
Published Articles