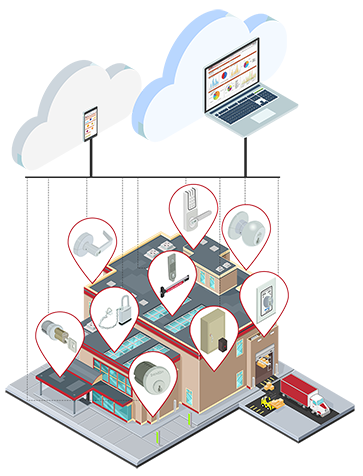
Get more than just locks and keys
No matter what needs securing, we provide economical mechanical and WiFi lock systems and an easy way to manage it all with:
- Immediately rekeyable locks & other hardware
- Easy-to-track keys that cannot be copied
- Cloud-based key management software
- A team of program experts ready to help
We Proudly Partner With:





.png?width=2000&name=LPRC%20logo%20(2e2e2e).png)



More than just a mechanical key system
Our Key Control Program is designed to maximize security and minimize costs through re-imagined hardware, cutting edge program record management and dedicated support.

Control Key System Costs

Spend Less Time Managing Locks & Keys

Improve Mechanical Key System Security



